Setting Report Security
An important EBMS data security consideration is to limit a user's access to reports. Reports can be secured by either of the following methods:
-
Blocking the user from the entire report: This common method is used to block certain users from having any access to a specific report.
-
Limiting a user's ability to change default prompts: Review the Prompt Security section below.
-
Customizing a report that removes sensitive information after verifying that another existing standard report does not contain the secure information: Review Crystal Reports Interface Overview for more information on report customization.
Database data field security settings explained in the previous section do not affect reports. For example, a secure field within a report will not be hidden because the user is barred from the field. The entire report must be secure to protect data within the report. Report security is set within individual reports.
Report Security
Go to File > Reports and select a report. With the selected report name highlighted, click on the Properties button to open the following dialog:
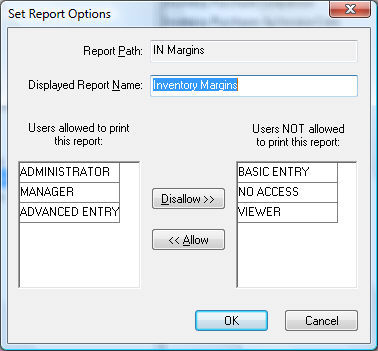
All users with permission levels that are included in the list on the left side of the dialog will be able to print the current report. All others listed on the right side of the list will not have access to the report. Use the Disallow and Allow buttons to move user permission levels to or from the Users allowed to print this report list and the Users NOT allowed to print this report list.
The user's security level for the specific report is determined by the first two initials of the report path. For example, the Report Path shown above is prefixed with the IN initials which links the report security to the Inventory security settings. Some other prefixes used by report security is as follows:
-
GL - General Ledger
- IN - Inventory
-
AP - Expenses (Accounts Payable)
-
AR - Sales (Accounts Receivable)
-
PY - Payroll
-
TA - Tasks
Prompt Security
A user can be restricted from changing report prompts in the following ways:
-
Set security settings for all prompts
-
Set security settings for individual prompts
Complete the following steps to restrict a user's ability to change a prompt:
-
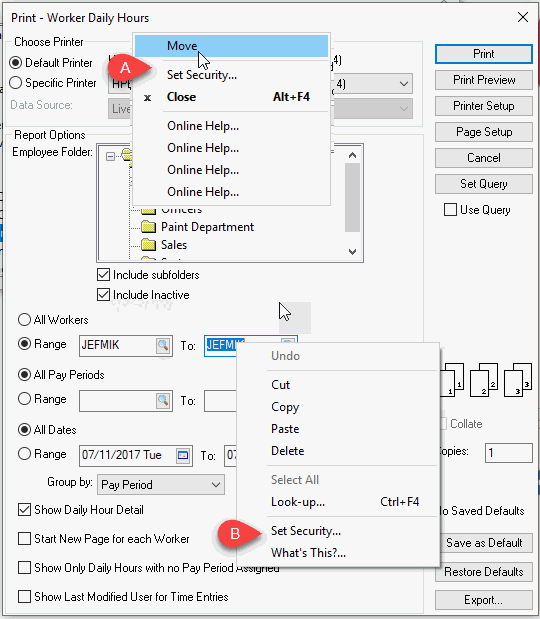
Open a report and click on the Print and Print Preview button to open the report prompt.
-
Right-click on the report title (A) or individual report prompts (B) and select Set Security from the context menu as shown above:
-
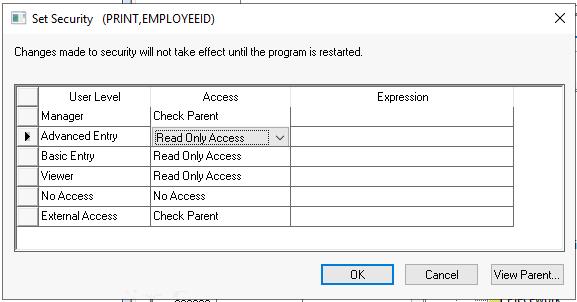
Set the desired security level for this report prompt. Do not use the View Parent button settings for reports. Review Setting Security for a Tab, Entry Field, Button, or Process for instructions on the following security settings.
-
Click OK and repeat for any other report prompts.
-
The users must restart EBMS for the report security to be valid.